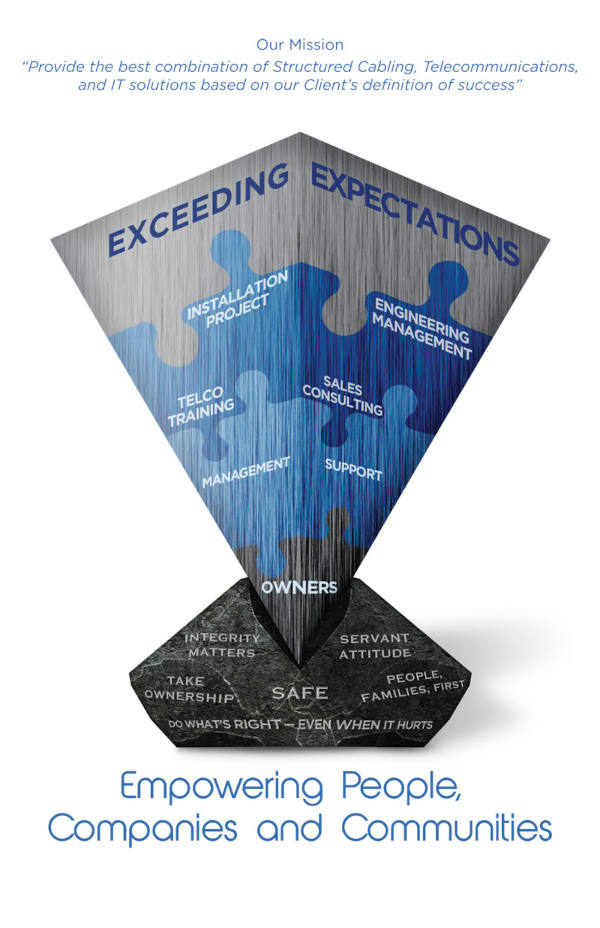
Why PacStates?
We negotiate, design, install, manage and support innovative solutions for your business communications. At the end of the day, we know how critical it is for your organization to stay connected. Consider us your advocates and full-service technology solution providers.
- Local 24/7 Service, Onsite and Remote.
- Your business uptime is our top priority.
- Systems Integrators – Analyzing your current and future needs, and working to develop solutions and timelines to ensure successful deployments.
- Constantly Evolving Expertise – Keeping up with technology advancements, education and available tools so you can concentrate on what you do best.
- Locally Owned and Operated Since 1986 and Committed to Our Community.